Splunk 搭建及使用
Splunk 搭建及使用
学习资料:
安装
图像化安装,不过多演示
落地
一般企业落地中使用Splunkforwarder 转发日志到Splunk Server。
使用
口令爆破
开启审核
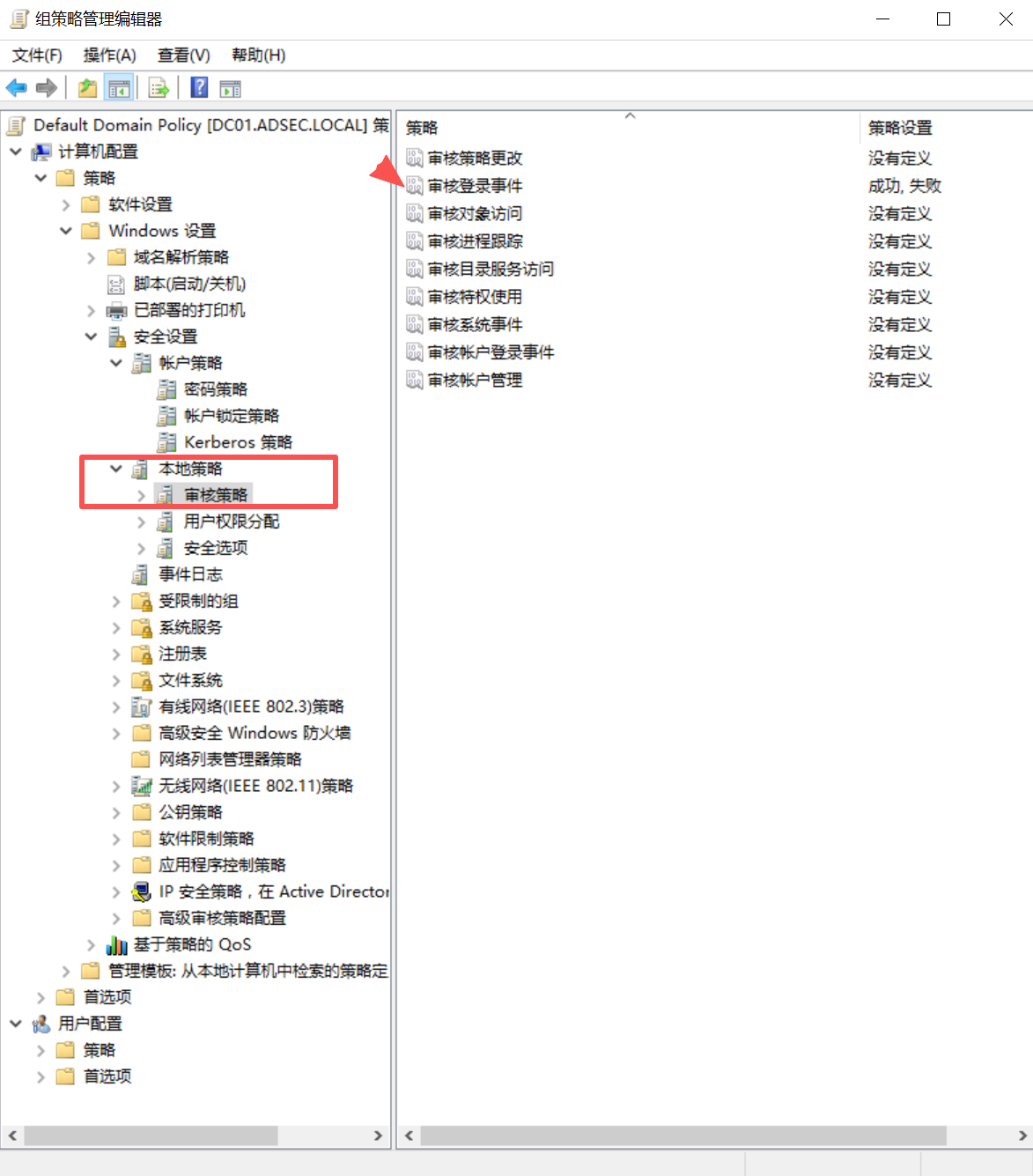
生成日志
nxc smb 192.168.116.5 -u administrator -p pass.txt -d adsec.local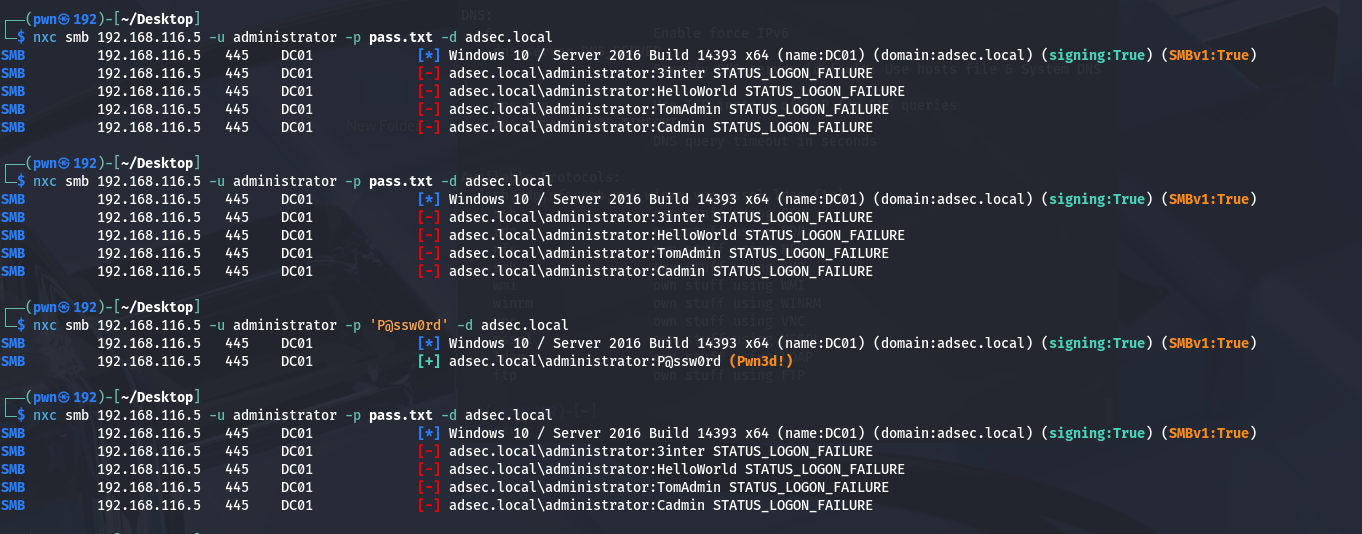
(index="ad" sourcetype=WinEventLog:Security (EventCode=4624 OR EventCode=4625)) | rex "帐户名:\s+(?<帐户名>[^\r\n]+)" | rex "Account Name:\s+(?<帐户名>[^\r\n]+)" | rex "用户名:\s+(?<帐户名>[^\r\n]+)" | rex "User Name:\s+(?<帐户名>[^\r\n]+)" | rex "Target User Name:\s+(?<帐户名>[^\r\n]+)" | bucket _time span=5m | stats min(_time) as start_time max(_time) as end_time count(eval(EventCode==4625)) as count_failure count(eval(EventCode==4624)) as count_success by 帐户名 | eval start_time=strftime(start_time,"%Y-%m-%d %H:%M:%S") | eval end_time=strftime(end_time,"%Y-%m-%d %H:%M:%S")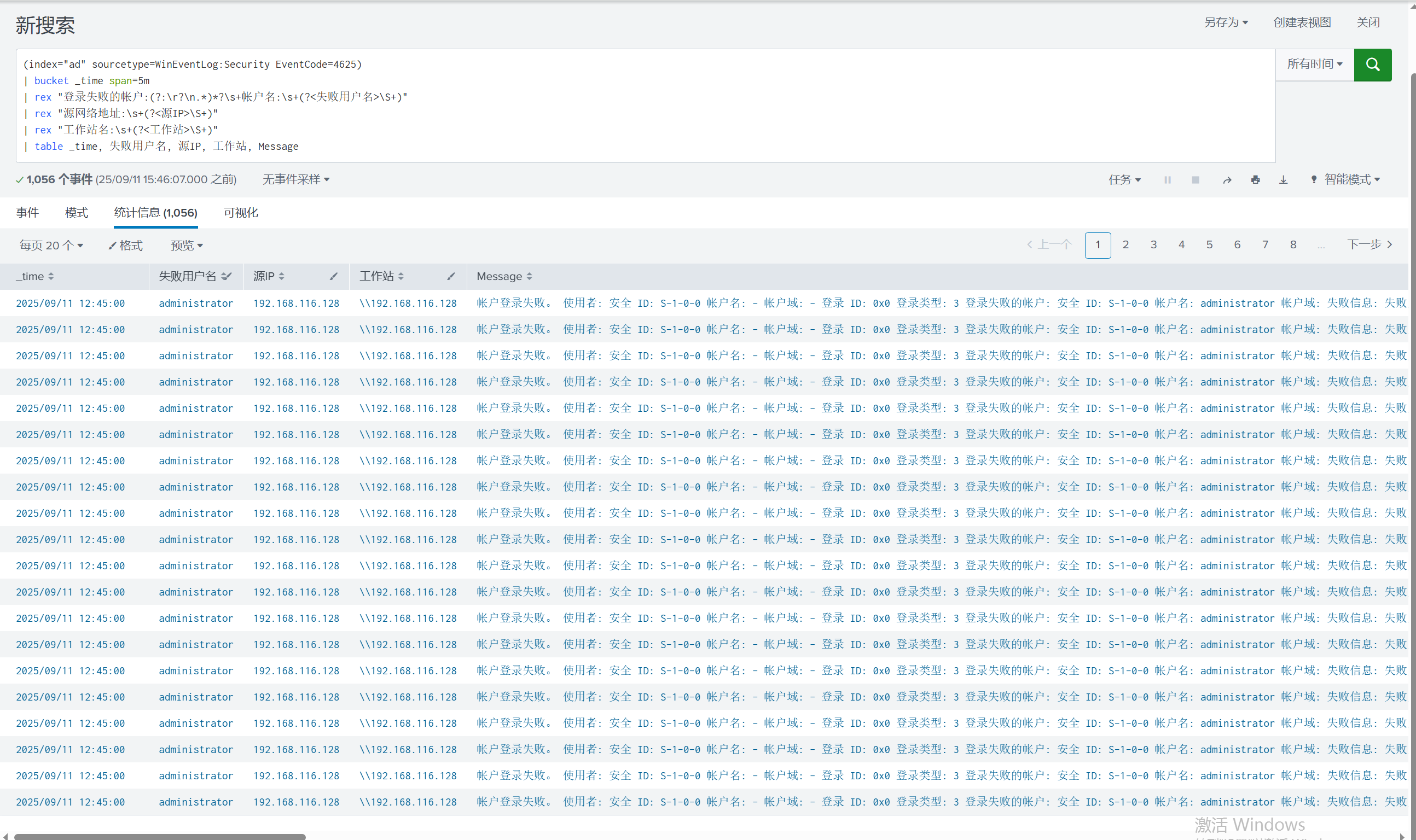
dcsync语法
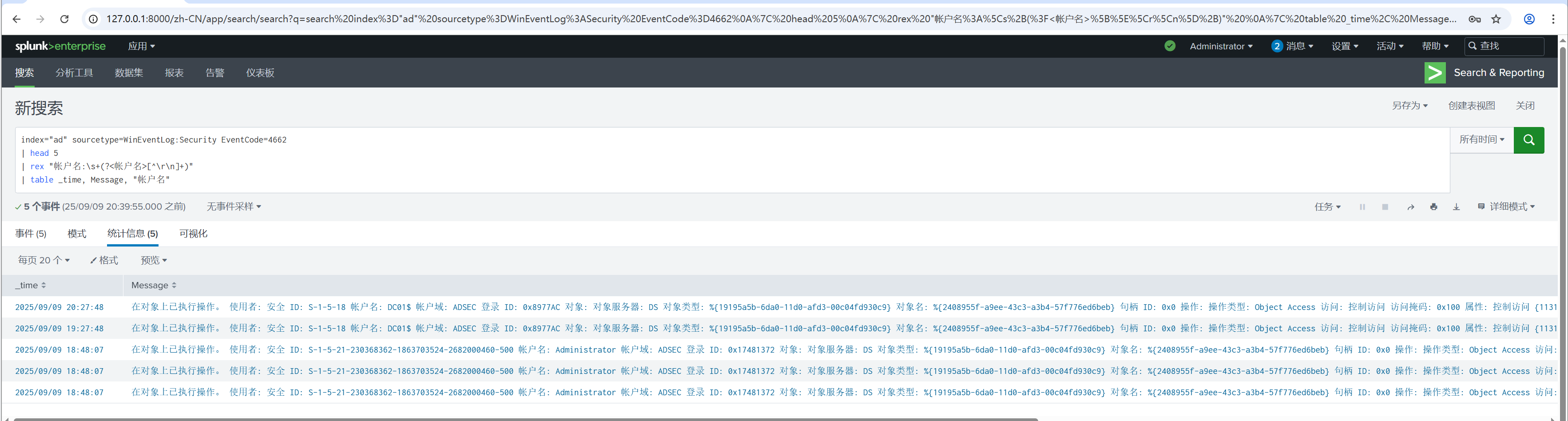
index="ad" sourcetype=WinEventLog:Security EventCode=4662 sourcetype=WinEventLog:Security EventCode=4662 ({1131f6aa-9c07-11d1-f79f-00c04fc2dcd2} OR {1131f6ad-9c07-11d1-f79f-00c04fc2dcd2}) | head 10 | rex "帐户名:\s+(?<帐户名>[^\r\n]+)" | table _time, Message, "帐户名"